Cybersecurity researchers are revealing malicious campaigns that use search engine optimization (SEO) addiction technology to provide a known malware loader called Oyster (aka Broomstick or Cleanuploader).
Malvertising activity per Arctic Wolf promotes fake websites that host troilerized versions of legal tools such as Putty and WinSCP, and aims to search for these programs and install them instead.
“At the time of execution, a backdoor known as Oyster/Broomstick was installed,” the company said in a simple matter that was released last week.
“Permanence indicates that you create a scheduled task that runs every 3 minutes, run a malicious DLL (Twain_96.dll) via rundll32.exe using DLLRegisterServer export, and use DLL registration as part of the persistence mechanism.”
Some fake website names are listed below –
Updaterputty[.]com zephyrhype[.]com putty[.]Running putty[.]Bets, and puttyy[.]Organization
The threat actors behind the campaign are suspected of targeting other IT tools to deliver malware, and it is essential for users to stick to trusted sources and official vendor sites to download the software they need.

This disclosure is used to search results for games related to AI-related keywords and to spread Vidar, Lumma, and Legion Loader.
These websites are equipped with JavaScript code that checks for the presence of ad blockers and collects information from the victim’s browser, and will eventually launch a redirect chain that takes the victim to a phishing page that hosts the ZIP archive.
“The final download page for this campaign offers Vidar Stealer and Lumma Stealer as password-protected ZIP archives, with passwords being provided on the final download page,” said Zscaler Threatlabz. “When extracted, it contains an 800MB NSIS installer. This is a bypass detection system, with a seemingly large size intended to look legal with file size limits.”
The NSIS installer is used to run the car script that is ultimately responsible for launching the Steeler payload. In contrast, Legion Loader’s delivery mechanism leverages the MSI installer to deploy malware via batch scripts.

It has been observed that similar SEO addiction campaigns raise phishing pages when users search for the names of popular web applications, forge CloudFlare Captcha check pages to drop Redline Stealer via Hijack Loader.
Small and medium-sized businesses (SMBs) are increasingly targeted by cyberattacks that provide malware disguised as collaboration tools such as Openai ChatGPT, Deepseek, Cisco AnyConnect, Cisco, Google Drive, Microsoft Office, Microsoft Teams, Microsoft Teams, and Salesforce, according to data compiled by Kaspersky.
“In January-April 2025 alone, approximately 8,500 SMEs were targeted by cyberattacks in which malware or potentially unwanted software was disguised as these popular tools,” the Russian cybersecurity company said.
Zoom accounts for around 41% of the total number of unique files, followed by 16% Outlook and PowerPoint, respectively, followed by Word at 12%, 9%, and team at 5%. In the first four months of 2025, the number of unique malicious files mimicking ChatGpt increased by 115% to 177.
The tendency to abuse fake search engine lists to use implicit users for popular users is a well-known tactic, but a recent campaign has hijacked searches for technical support pages linked to Apple, Bank of America, Facebook, HP, Microsoft, Netflix, and PayPal.
“Visitors are taken to the Help/Support section of the brand’s website, but instead of a real phone number, the hijacker will display the scammer number instead,” says MalwareBytes.
This is accomplished by a technique called search parameter injection, which displays numbers under attacker control within the search bar, gives the impression that they are official search results within the Help Center page, and deceives them to call unsuspecting users.
What makes the attack particularly insidious is that parameters added to the right of the actual Help Center domain (e.g. “Call ***-**-** for free”) are not visible in sponsored search results.
It’s not just Google’s advertising platform. Threat actors have also been caught up in line with the annual event linked to Pi2day, offering fake ads to Phish on Facebook for the Cryptocurrency Wallet Recovery phrase, along with Pi networking community.
The malware spreads through ads that encourage users to install new versions of the PI Network Desktop App for Windows, stealing stored credentials and Crypto wallet keys, logging user input and downloading additional payloads.
Romanian cybersecurity firm Bitdefender said the activity could possibly be the job of a single threat actor, “implementing parallel fraud schemes in the meta to maximize reach, financial profits and targeting efficiency.”
Fake websites that impersonate AI, VPN services, and other well-known software brands have been found to provide loaders called Paseidon Stealer and Payday Loader on Macos systems. This activity has been called the codenamed Dark Partner by security researcher G0NJXA.
Payday Loader relies on Google Calendar Links to extract command and control (C2) servers and retrieve obfuscated JavaScript code designed to load Lumma Stealer Payload and Siphon-sensitive data, relying on as a Dead Drop Resolver.

Interestingly, the email address used to create Google Calendar events (“eceverridelfin@gmail[.]com”) was found in connection with a malicious NPM package called “OS-INFO-Checker-ES6”. This indicates that dark partner actors are likely experimenting with different delivery mechanisms.
“Payday Loader has a node.js Stealer module for removing Cryptocurrencies Wallet Data from external C2,” G0njxa said. “Using the ADM-ZIP library in node.js, Payday Loader can find, package and send wallet information to hard-coded C2 hosts.”

These campaigns work with the ongoing phenomenon in which scammers and cybercriminals set up a vast network of thousands of websites to commit financial fraud by spoofing popular brands and promoting real products that are never offered. Such a network is called GhostVendors by Silent Push, and has bought Facebook ad space to promote over 4,000 sketchy sites.
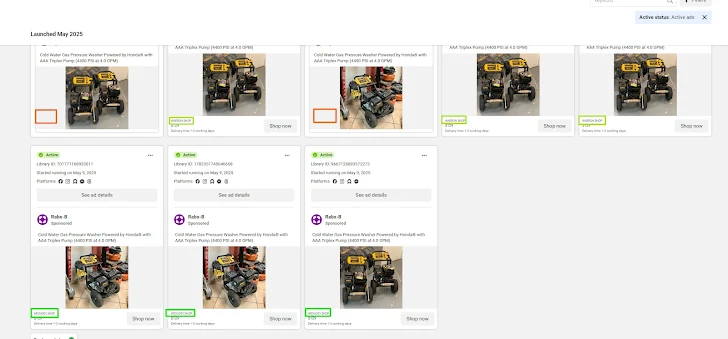
Malicious Facebook Market ads run for several days, then halt, effectively removing all of their traces from the meta ad library. It is worth pointing out that Meta has remained only advertising on social issues, elections and politics for the past seven years.
“This helped us to ensure that there are known meta-advertising library policies and highlighted that these threat actors may be taking advantage of this by quickly launching and halting advertisements for similar products on various pages.”
Another network discovered by companies targeting English and Spanish shoppers with fake market ads is being rated as the work of Chinese threat actors. These websites are primarily designed to steal credit card information entered on payment pages while insisting on processing your order. Some fake sites also include a Google Pay purchase widget to enable payments.
“This fake market campaign is primarily targeting consumers with the threat of phishing that leverages the fame of major brands, well-known organizations and several political figures,” Silent Push said.
Source link