The Ukrainian Computer Emergency Response Team (CERT-UA) is using a backdoor called the Cabinettrat to warn of new, targeted cyberattacks in the country.
The activity observed in September 2025 is attributed to a threat cluster tracking as UAC-0245. The agency said it discovered the attack after a software tool that took the form of an XLL file was discovered.
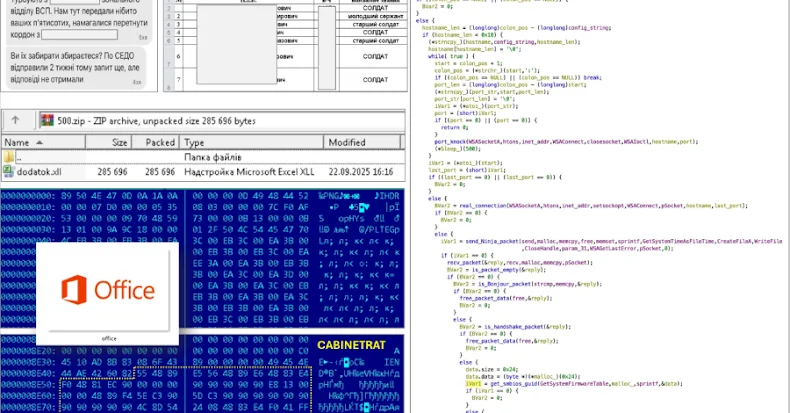
Further investigation revealed that the XLL files were distributed within a ZIP archive shared by signal messaging apps, disguised as documents regarding the detention of individuals who attempted to cross the Ukrainian border.

XLL is designed to create numerous executables on compromised hosts, namely the exe file in the startup folder, an xll file called “basicexcelmath.xll” named “basicexcelmath.xll”.
Changes to the Windows registry are made to ensure the persistence of the executable. Then, in order to finally run the XLL add-in, launch the excel application (“excel.exe”) in hidden mode with the “/e” (“/embed”) parameter. The main purpose of XLL is to parse and extract from PNG file shellcodes classified as CabineTrat.
Both the XLL payload and shellcode are equipped with many anti-VM and anti-analysis procedures to avoid detection, including the presence of tools such as VMware, Xen, QEMU, Parallel, Hyper-V, at least two processor cores and at least 3GB of RAM checks.
A full-fledged backdoor written in the C programming language, CabineTrat is primarily designed to enumerate system information, installed programs, a list of screenshots, and directory contents, allowing you to delete specific files or directories, and perform file upload/downloading. Communicates with the remote server over a TCP connection.
The disclosure comes days after Fortinet Fortiguard Labs warned of attacks targeting Ukraine by harvesting targeted data from Ukrainian national police, harvesting sensitive data from target systems, and impersonating Ukrainian national police in a fireless phishing campaign to mine cryptocurrency.
Source link