Cybersecurity researchers have flagged Ukrainian IP networks to engage in a massive brute force and password spray campaign targeting SSL VPNs and RDP devices from June to July 2025.
This activity stemmed from the Ukraine-based autonomous system FDN3 (AS211736), each French cybersecurity company Intrinsec.
“We believe FDN3 is part of a wider abusive infrastructure consisting of two other Ukrainian networks (AS61432) and Erishennya-ASN (AS210950), as well as a Seichel-based autonomous system named TK-Net (AS210848).
“All of these will be allocated in August 2021, and in many cases we will exchange IPv4 prefixes with each other to avoid block lists and continue to host abusive activities.”
AS61432 is currently announcing a single prefix of 185.156.72[.]On 0/24, AS210950 announced two prefixes 45.143.201[.]0/24 and
185.193.89[.]0/24. The two autonomous systems were assigned in May and August 2021, respectively. The majority of the prefixes were also announced at AS210848, another autonomous system assigned in August 2021.

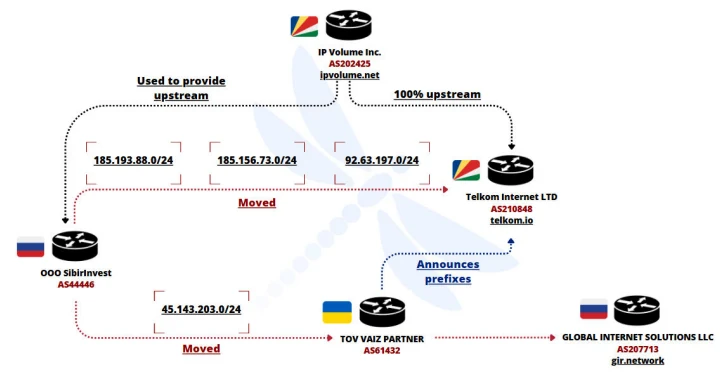
“The network is based in the Seychelles and shares all peering agreements with IP Volume Inc. (AS202425), created by the owner of Extel. Since 2005, it has been infamous for running a significantly abusive bulletproof hosting service in the Netherlands.”
The entire prefix, moved from AS61432 and AS210950, has been announced by bulletproof and abusive networks that have been brought to the forefront by shell companies such as Globl Internet Solutions LLC (GIR.Network), Global Connectivity Solutions LLP, Verasel, IP Volume Inc. and Telkom Internet Ltd.
The findings were built on previous disclosures about how multiple networks were allocated in August 2021 and based in Ukraine and the Seychelles (AS61432, AS210848, and AS210950). In June 2025, some of the IPv4 prefixes announced by these networks were moved to FDN3, which was created in August 2021.
That’s not all. One by three prefixes published by AS210848 and AS61432 was previously announced by another Russian network Sibirinvest OOO (AS44446). Of the four IPv4 prefixes announced by FDN3, one of them (88.210.63[.]0/24) is rated as previously announced by a US-based bulletproof hosting solution named Virtualine (AS214940 and AS214943).

This IPv4 prefix range is attributed to large brute force and password spray attempts, with activity scaling to record highs between July 6th and 8th, 2025.
Bruteforce and password dissemination efforts for SSL VPNs and RDP assets could last up to three days, according to Intrinsec. Note that these techniques are employed by various ransomware (RAAS) groups such as Blackbusta, Global Groups, and Ransom Hubs as initial access vectors for breaching corporate networks.
Two other prefixes announced by FDN3 at 92.63.197[.]0/24 and 185.156.73[.]0/24 was previously announced by AS210848 and shows advanced operational overlap. 92.63.197[.]0/24 has connections with Bulgarian spam networks like Roza-AS (AS212283).
“These powerful similarities, including configuration, host content, and creation dates, have all come to appreciate the aforementioned autonomous systems operated by a typical bulletproof hosting administrator with a high level of confidence,” explained Intrinsec.

Further analysis of FDN3 revealed its relationship with a Russian company called Alex Host LLC. It was linked to bulletproof hosting providers such as TNSecurity, which are used to host the Doppelganger infrastructure.
“This study again highlights the common phenomenon of offshore ISPs such as IP Volume Inc., enabling smaller bulletproof networks through peering contracts and prefix hosting,” the company said. “Thanks to offshore locations such as Seychelles, which provide anonymity to owners of these companies, malicious activities carried out through those networks cannot be attributed directly to them.”
This development is because Cansys discovered a connection backproxy management system associated with a Polared Botnet, currently running on more than 2,400 hosts. This system is an RPX server that acts as a reverse connect proxy gateway that manages proxy nodes and can expose proxy services.
“The system looks like a well-designed server that could be one of many tools used to manage Polared Botnets,” said security researcher Mark Elsie. “This particular service is completely unrelated to Polaredge and could also be a service that BotNet uses to jump between different relays instead.”
Source link