“Living off the land” has become a preferred tactic for threat actors in many attack scenarios. This time, an existing “innocuous” component is being used as part of a phishing campaign. By leveraging the reputation of trusted services like PayPal and Zoom, attackers can bypass traditional Secure Email Gateways (SEGs) that whitelist these domains.
Recently, Prophet AI investigated a phishing alert that was found to be related to a highly sophisticated variation of this tactic, a Telephone Oriented Attack Delivery (TOAD) campaign armed with Zoom’s own authentication infrastructure.
This research highlights not only the ingenuity of modern attackers, but also the need for AI-driven analysis that goes beyond validated headers to understand the intent within them.
Attack: Weaponize your “display name”
The attack vectors identified by Prophet AI are elegant in their simplicity, but dangerous in their execution. Unlike standard phishing emails that spoof domains, this attack generates legitimate emails from Zoom itself.
The mechanisms used by the attackers are:
Account Creation: The attacker registers a new Zoom account using an email address they control. Payload injection: Sets the account’s “display name” to a fraudulent emergency message instead of the real name. In this particular case:
“Dear Customer, $989.95 USD will be automatically debited from PayPal. If you believe you are not who you say you are, please call PayPal now at +1-805-400-XXXX.” Trigger and Delivery: The attacker sets up an email account to automatically forward the message to the victim. You will then attempt to log into your Zoom account and Zoom will send you a standard one-time password (OTP) email.
Result: Victim receives forwarded email. Emails are sent from Zoom’s official infrastructure, so they pass standard authentication checks (SPF/DKIM). When a victim opens it, the Zoom template reads, “Hello customer, your PayPal will be automatically debited…”
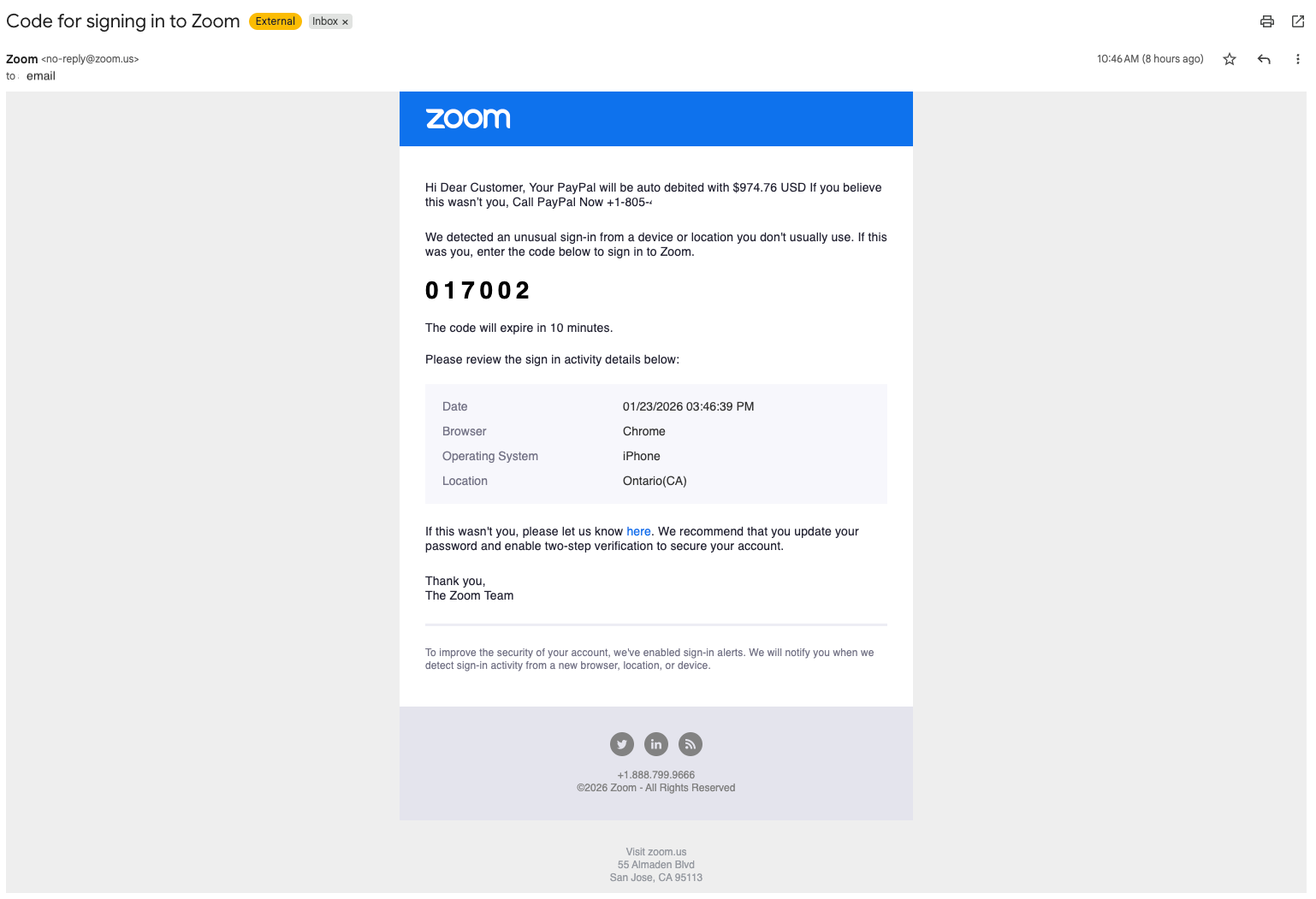
This technique creates a “verified” Trojan. This email is technically safe and contains no malicious links or malware. However, the text itself is a social engineering trap designed to panic users into calling a fraudulent support number.
Prophet AI Investigation
While traditional filters might show “secure” emails from zoom.us or forwarded messages with valid headers, Prophet AI analyzes the content’s contextual intent.
Upon processing the raw email, Prophet AI immediately flagged the message even though it came from a legitimate source.
In this case, Prophet AI ran 138 queries against 11 data sources, all in just 5 minutes.
why is this important
This attack mirrors obfuscation techniques seen in recent campaigns, where the payload is hidden in plain sight within the legitimate field of a trusted service.
The specific danger here is a decline in trust. Users are trained to look for legitimate senders. When you see an email from a real Zoom (or an email forwarded from a real sender), you’ll be less wary. Attackers use this “halo effect” to evade surveillance.
By identifying mismatches between the sender (Zoom) and the content (PayPal’s financial urgency), Prophet AI was able to identify a trap as an actual attack before any financial loss was incurred.
Stay alert and evolve your phishing research
As attackers continue to exploit the capabilities of the tools we use every day, the definition of “malicious email” will need to evolve as well. Verifying the sender of an email is no longer enough. You need to see what they have to say.
The analysis required in these cases goes beyond some of the static playbooks typically used by Level 1 analysts. This is a classic case that confuses junior analysts and requires escalation to level 2. While many AI SOC products focus on automating typical L1 alert triage, Prophet AI goes beyond that to not only save time on typical L1 tasks, but also reduce the overhead of more expensive L2 and L3 resources.
These attacks are more complex, and reported phishing and email alerts require complex investigation that cannot be performed efficiently using a human-only approach. Prophet AI adds machine-level scale and speed while performing thorough and complete analysis. Deploying Prophet AI to phishing is an easy way to improve your findings while controlling costs and reducing your MTTR to a level that keeps pace with today’s high-velocity threats.
Prophet Security responsibly reported the attack method and use of Zoom resources to Zoom prior to publishing this analysis.
.jpg)
Source link

