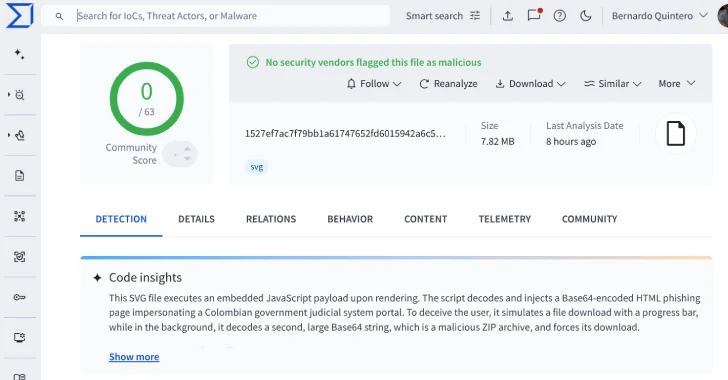
Cybersecurity researchers are flagging new malware campaigns that leverage scalable vector graphics (SVG) files as part of a phishing attack that impersonates the Colombian judicial system.
According to Virustotal, SVG files are distributed via email and designed to run embedded JavaScript payloads. This will embellish the Base64-encoded HTML phishing page as a portal for Fiscalía General De la Nación, the Department of Justice Bureau of Colombia.
This page simulates the official government document download process with a fake progress bar, but it causes stealthy ZIP archive downloads in the background. The exact nature of the zip file is not disclosed.
According to a malware scanning service owned by Google, 44 unique SVG files were found. All of these are not detected by the antivirus engine, as they avoid static detection methods using techniques such as obfuscation, polymorphisms, and large amounts of junk code.
In total, 523 SVG files have been detected in the wild, with the earliest samples dating back to August 14th, 2025.

“Looking deeper, we found that the earliest sample was large, about 25 MB, with size decreasing over time, suggesting that attackers are evolving their payload,” Virustotal said.
This disclosure uses cracked versions of legal software and click-fix style tactics to seduce users to infect information steel called Atomic MacOS Stealer (AMOS), exposing businesses to qualify, financial theft, and other follow-on attacks.
“AMOS is designed for a wide range of data theft that allows you to steal files from credentials, browser data, cryptocurrency wallets, telegram chats, VPN profiles, keychain items, Apple notes, and general folders,” Trend Micro said. “Amos shows that Macos is no longer a peripheral target. As MACOS devices gained evidence in corporate settings, they became a more attractive and profitable focus for attackers.”
Attack chains essentially involve targeting users looking for cracked software on sites like Haxmac[.]Trigger AMOS deployment by redirecting them to the Bogus download link, which provides installation instructions designed to run malicious commands in the terminal app.
It is worth noting that Apple prevents the installation of .DMG files, which lacks proper notarization for gatekeeper protection on MacOS.

“With the release of MacOS Sequoia, attempts to install malicious or unsigned .DMG files, such as those used in AMOS campaigns, are blocked by default,” the company added. “This doesn’t completely eliminate the risk, but it poses barriers to successful infections and allows attackers to adapt their birth method, especially for users who may bypass built-in protection.”

This is why threat actors are increasingly putting banks in their banks with Clickfix. Because you can use the terminal to install the steeler on your machine using the Curl command specified on the software download page.
“While MacOS Sequoia’s enhanced gatekeeper protection successfully blocked traditional .DMG-based infections, threat actors were quickly pivoted to terminal-based installation methods that have proven to be effective bypassing security controls,” Trend Micro said. “This shift highlights the importance of detailed strategies that do not rely solely on built-in operating system protection.”
The development follows the discovery of a “spread cyber campaign” targeting gamers looking for cheats for Stealc Stealer and Crypto Theft Malware, which has earned more than $135,000 in threat actors.
The activity for each Cyberark is notable to take advantage of STEALC’s loader functionality to download additional payloads.
Source link