The China-related threat actor known as Winnti is attributed to a new campaign called Revival Stone in March 2024 that targeted Japanese companies in the manufacturing, materials and energy sectors.
Activities detailed by Japanese cybersecurity company LAC overlap with EARTH FREYBUG tracked by Trend Micro. It is rated as a subset within the APT41 Cyberspy Group and is rated by Symantec As As Symantec by the Cyberseason under Operation Cuckoobees. Black Fly.
APT41 is described as a highly skilled and systematic actor with the ability to not only poison the supply chain, but also carry out spy attacks. Its campaigns are often designed with stealth in mind, not only bypassing security software installed in your environment, but also harvesting important information and secrets for persistent remote access. Not only will you establish a channel for, but you will also use a swarm of tactics to achieve your goals.

“Many of the group’s espionage is consistent with the national strategic goals, targeting a wide range of public and private industry sectors around the world,” Lac says.
“The attacks of this threat group are characterized by the use of Winnti malware. Winnti malware has its own rootkit that allows communication to be hidden and manipulated, and legitimate digital certificates stolen from the malware can be used.
Winnti, which has been active since at least 2012, has picked out manufacturing and materials-related organizations primarily in Asia as of 2022 and has run a recent campaign between November and October 2023. IBM Lotus Domino deploying malware as follows:
Deathlotus – Passive CGI backdoor that supports file creation and command execution Defense Evasion Utility written in Unapimon-C++ Privatelog – The loader used to drop Winnti Rat (aka DeployLog) is named Winnkit is used to provide a kernel-level Rootkit. rootkit installer means cunningpigeon – Use the Microsoft Graph API to use commands (file and process management, and custom proxy) to enable rootkit with the ability to intercept TCPIP network interfaces, and to use infected cover channels. Create endpoint shadowgaz in an intranet – Passive backdoor reuse of listening ports from IIS web server
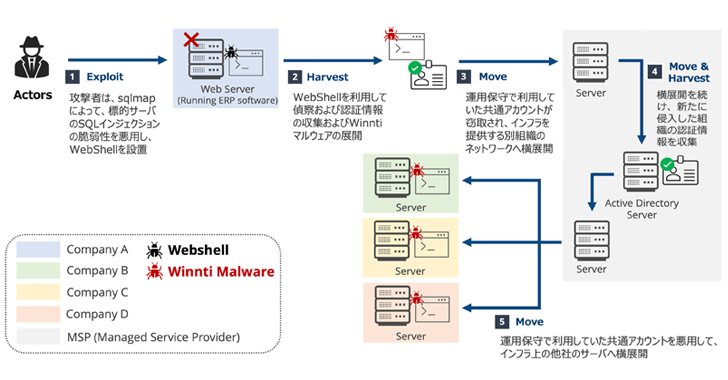
The latest attack chain documented by LAC takes advantage of a SQL injection vulnerability in unspecified enterprise resource planning (ERP) systems to web shells such as Chinese choppers and Behinder on compromised servers (aka Bingxia) and Icecorpion (Icecorpion) and drop using access. To perform reconnaissance, collect lateral movement credentials and provide an improved version of Winnti malware.

Intrusion reach is further expanded to managed service providers (MSPs) by leveraging shared accounts, and then further expanded by weaponizing the company’s infrastructure and propagating the malware further to three other organizations. It is said that it was done.
Luck said that references to Treadstone and Stonev5 were also found in the Revivalstone campaign. The former is a controller designed to work with Winnti malware, and was also included in last year’s I-Soon (aka Ancan) leak. Linux Malware Control Panel.

“If treadstones have the same meaning as winnti malware, that’s just speculation, but Stonev5 could mean version 5, and the malware used in this attack could be Winnti v5.0. It’s sexual.”
“The new Winnti malware is implemented with features such as obfuscation, updated encryption algorithms, and security products avoidance, and this group of attackers may update the Winnti malware features and continue to use them in attacks. there is.”
This disclosure has been made since November 2024, a Linux-based attack called SSHDInjementor, which was equipped to hijack SSH daemons on network appliances by injecting malware for permanent access and concealment actions. We’ve explained the suite in detail.
A malware suite associated with another Chinese nation-state hacking group known as Daggerfly (aka Bronze Highland and Evasive Panda) is designed for data removal, and hears incoming orders from remote servers, allowing you to access and execute processes and Enumerate services, perform file operations, perform file operations, and perform file operations. Start the terminal and execute the terminal command.
Source link