BUZZY CHINESE The Startup Deepseek, a startup of artificial intelligence (AI), has recently become popular, and one of the databases has been released on the Internet, so malicious actors can access confidential data.
According to Wiz Security Researcher Gal Nagli, the clickhouse database states that “the database operations can be completely controlled, such as the functions that access internal data.”
Exposure also contains more than 1 million logstream, including chat history, secret key, backend details, and very sensitive information such as API secrets and operation metadata. Later, DeepSeek presented a security hole after the cloud security company was about to contact.

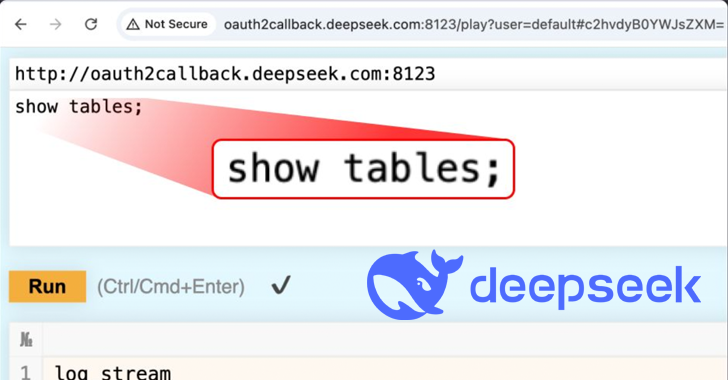
Hosted in OAuth2callback.deepseek[.]COM: 9000 and Dev.deepSeek[.]COM: 9000 is said to have enabled unauthorized access to a wide range of information. According to Wiz, complete database control and potential privilege escalation in the DeepSeek environment are now possible without the need for authentication.
This included the clickhouse HTTP interface to perform any SQL query directly through a web browser. It is currently unknown whether other malicious actors have seized the opportunity to access or download data.
“A quick recruitment of a corresponding security AI service is essentially dangerous,” Naguri stated in a statement shared with hacker news. “Many of the AI security precautions focus on future threats, but the actual danger often comes from basic risks, such as accidental exposure of the database.”
“Protection of customer data must continue to be a priority for security teams. It is important for security teams to work closely with AI engineers to protect data and prevent exposure.”


DeepSeek is a topic of AI circles of the innovative open source model that claims to oppose major AI systems such as Openai, and is efficient and cost -effective. The reasoning model R1 is praised as the “moment of SPUTNIK of AI”.
UPSTART’s AI chatbot competes to the top of the App Store chart crossing Android and iOS in some markets, despite being the target of “large -scale malicious attacks”. We are urging you to stop.
In an update posted on January 29, 2025, the company stated that it was identifying this issue and working on the implementation of corrections.
At the same time, the company was also on the receiver of the scrutiny of the privacy policy, but it was a matter of US national security concerns, of course.

In addition, DeepSeek apps have become unusable in Italy after demanding information about data processing practices and information about the location where Garante, a national data protection regulatory authority, acquired the training data. It is unknown whether the withdrawal of the app responds to the question from the watchdog. Similar demands were also sent by Ireland’s Data Protection Committee (DPC).
The Bloomberg, Financial Times, and the Wall Street are also reporting that both Openai and Microsoft are using Openai’s application program (API). I am. 。
“We know the group [China] We are actively working to use a method that contains what is called distillation and use a method of duplicating advanced US AI models, “said Openai’s spokeswoman. 。
Source link