A new finding from Garderio Labs shows that a combination of propagation methods, narrative refinement, and avoidance techniques has helped remove the way a social engineering tactic called Clickfix has been taking place over the past year.
“Like a real-world virus variant, this new ‘clickfix’ strain quickly rose, eventually finally wiping away the infamous fake browser update scam that plagued the web last year.”
“We did so by removing the need to download files, using smarter social engineering tactics and spreading through reliable infrastructure. The result – a wave of infection from mass drive-by attacks to hyper-targeting spearfishing lures.”
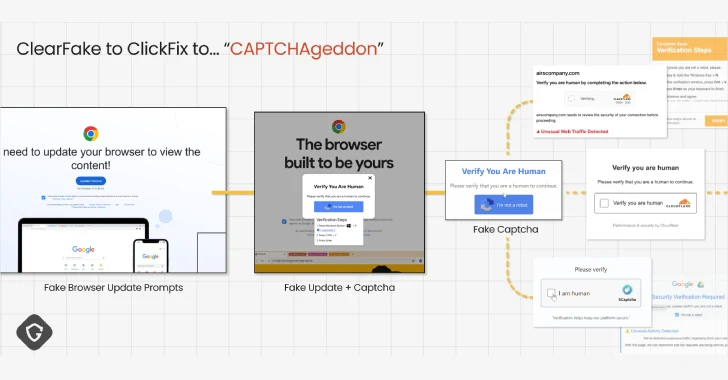
Clickfix is the name given to social engineering tactics where future targets are deceived to infect their machines, pose as if they were to fix non-existent issues or Captcha validation. It was first detected in the wild in early 2024.

These attacks use a variety of infection vectors, including phishing emails, drive-by downloads, fraud, and search engine optimization (SEO) addictions, to instruct users to fake pages that display error messages.
These messages have one goal. For Apple MacOS, victims will guide them to follow a series of steps to copy secretly copied malicious commands to the clipboard when pasted into the Windows Run dialog box or terminal app.

Nefarious Command triggers the execution of multi-stage sequences that lead to the deployment of various types of malware, such as steelers, remote access trojans, and loaders, highlighting the flexibility of the threat.
The tactics have become so effective and powerful that it leads to what Guardio calls Capt Chageddon, and actors from both Cybercriminal and Nation-State have equipped them in dozens of campaigns in a short period of time.
Clickfix is a more stealthy mutation in Clearfake, involving leveraging compromised WordPress sites to provide fake browser update pop-ups that provide Stealer malware. Clearfake then incorporated advanced evasion tactics like EtherHiding and used Binance’s Smart Chain (BSC) contract to hide the next stage payload.

Guardio said the evolution of Clickfix and its success was the result of constant improvements in terms of propagation vectors, lures and messages diversification, and the various methods used to advance the detection curve.
“The early prompts were common, but they were immediately persuasive and added clues of urgency and doubt,” Chen said. “These tweaks increased compliance rates by leveraging basic psychological pressures.”

Some of the notable ways that the attack approach has adapted include the abuse of Google scripts to host fake Captcha flows, thereby leveraging Google’s domain-related trust and embedding payloads in legitimate, good looking file sources such as socket.io.min.js.
“Obfuscation, dynamic loading, legitimately good looking files, cross-platform handling, third-party payload delivery, and abuse of trusted hosts like Google show how threat actors have continuously adapted to avoid detection,” added Chen.
“These attackers not only refine their fishing lures and social engineering tactics, but also remind us that their attacks invest heavily in technical methods to remain effective and resilient towards security measures.”
Source link