Cybersecurity researchers have presented new findings related to security issues related to communication protocols that can be abused by attackers and misused by attackers by known servers.
The vulnerability tracked as CVE-2025-49760 (CVSS score: 3.5) has been described by the Tech giant as a spoofing bug in Windows storage. Corrected in July 2025 as part of the monthly patch Tuesday update. Details of the security flaw were shared by Safebreach researcher Ron Ben Yizhak at this week’s DEF Con 33 security conference.
“External control of Windows storage filenames or paths allows certified attackers to perform spoofing on the network,” the company said in an advisory released last month.
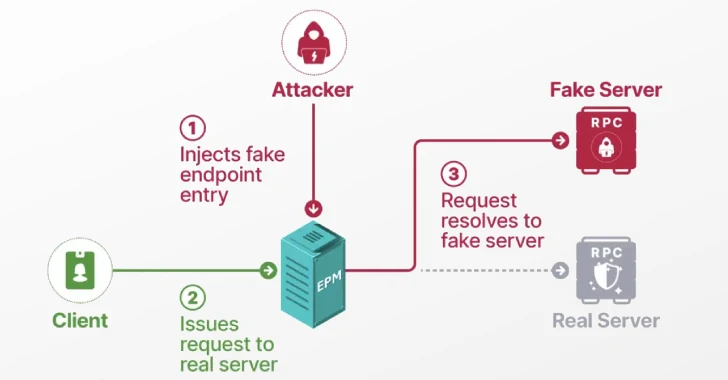
The Windows RPC protocol uses a universally unique identifier (UUID) and endpoint mapper (EPM) to connect an RPC client to the server-registered endpoint to enable the use of dynamic endpoints in client-server communications.
The vulnerability essentially allows it to be set in what is called EPM addiction attacks, which allow unprivileged users to pose as a legal, built-in service, with the aim of maintaining a protected process to manipulate core components of the RPC protocol and authenticate against any server of the attacker’s choice.
Given that the functionality of EPM is similar to that of the Domain Name System (DNS), it maps the interface uuid to the endpoint. Only DNS resolves a domain to an IP address. Attacks play like DNS addiction.
RPC clients poisoning EPM Masquerade as legitimate RPC servers achieve local/domain privilege escalation via ESC8 attacks
“We were shocked that nothing was preventing us from registering known built-in interfaces belonging to the Core Services,” Ben Ijak said in a report she shared with Hacker News. “For example, if a Windows Defender had a unique identifier, we expected that other processes would not be able to register, but that wasn’t the case.”

“When I tried to register an interface for a service that was turned off, the client connected to me instead. This discovery was incredible. There were no security checks completed by EPM.
The heart of an attack relies on finding interfaces that are not mapped to the endpoint. Also, many services are set to “delayed start” for performance reasons, allowing them to register immediately after the system boot by making the boot process faster.
In other words, services with manual startup are a security risk, as RPC interfaces are not registered for boot. By allowing attackers to register the interface before the original service, it is effectively susceptible to hijacking.

SafeBreach flags unstable RPC services (such as storage services and StorSVC.DLL), releases a tool called RPC-Racer that can be used to operate protected process lights (PPLs), allowing machine accounts to the servers selected by the attacker.
PPL technology ensures that the operating system only loads reliable services and processes, protecting the running process from termination or infection by malicious code. It was introduced by Microsoft in the release of Windows 8.1.
At a high level, the entire attack sequence is as follows:
Creates a scheduled task that will run when the current user logs in. Registers the storage service interface to trigger the delivery optimization service to send RPC requests to the storage service, connects to the attacker’s dynamic endpoint and calls the method. Machine account credentials leaking NTLM hash stage relays forced NTLM hash to web-based certificate enrollment service (AD CS) and leaks ESC8 attacks to achieve privilege escalation

To achieve this, you can use an offensive open source tool like Certipy to request a Kerberos Ticket Cultivation Ticket (TGT) using a certificate generated by passing NTLM information to an AD CS server, and use it to dump all the secrets from the domain controller.
Safebreach said it could further extend its EPM addiction technology to carry out interim (AITM) and denial of service (DOS) attacks by forwarding requests to the original service or registering many interfaces each to deny the request. The cybersecurity company also noted that there could be other clients and interfaces that are vulnerable to EPM addiction.
To better detect these types of attacks, security products can use event tracing in Windows (ETW), a security feature that monitors calls to RPCEPregister and records events raised by user-mode applications and kernel-mode drivers.
“You need to verify the identity of your RPC server so that SSL pinning ensures that the certificate is not only valid, but that it uses a specific public key,” says Ben Yizhak.
“The current design of the Endpoint Mapper (EPM) does not perform this validation. Without this validation, the client accepts data from unknown sources. By blindly trusting this data, the attacker can control the client’s actions and manipulate the attacker’s will.”
Source link