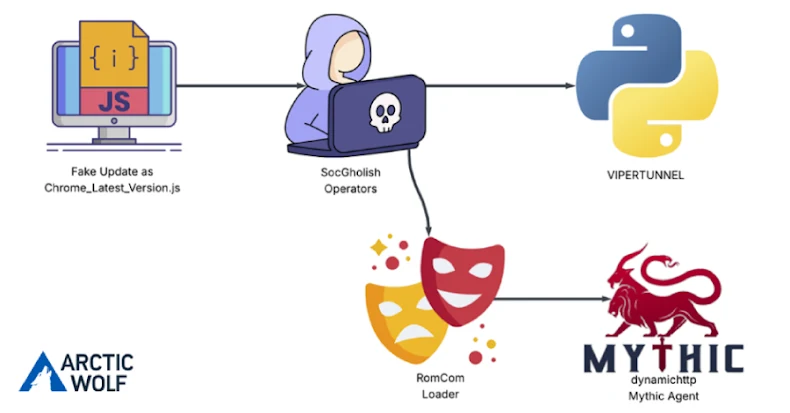
The attackers behind the malware family known as RomCom targeted a US-based civil engineering company via a JavaScript loader called SocGholish and delivered the Mythic Agent.
“This is the first time a RomCom payload has been observed being distributed by SocGholish,” Arctic Wolf Labs researcher Jacob Faires said in a report Tuesday.
This activity is believed to be carried out by Unit 29155 of the General Staff of the Armed Forces of the Russian Federation, also known as the GRU. The cybersecurity firm said the targeted organization had previously worked in a city with close ties to Ukraine.

SocGholish (aka FakeUpdates) is linked to a financially motivated operator tracked as TA569 (aka Gold Prelude, Mustard Tempest, Purple Vallhund, UNC1543) and acts as an initial access broker, allowing other threat actors to drop a wide range of payloads. Known customers include Evil Corp, LockBit, Dridex, and Raspberry Robin.
The attack chain typically involves delivering a fake Google Chrome or Mozilla Firefox browser update alert on a legitimate website, tricking unsuspecting users into downloading malicious JavaScript that causes the loader to be installed and fetch additional malware.
In most cases, attacks identify poorly secured websites and leverage known security vulnerabilities in plugins to inject JavaScript code designed to display pop-ups and activate infection chains.
Meanwhile, RomCom (also known as Nebulous Mantis, Storm-0978, Tropical Scorpius, UNC2596, or Void Rabisu) is the name assigned to a Russian-aligned threat actor known to dabble in both cybercrime and espionage since at least 2022.
Attackers utilize several methods, including spear phishing and zero-day exploits, to infiltrate target networks and drop their eponymous remote access Trojans (RATs) on victim machines. The hacker group’s attacks targeted not only NATO-affiliated defense organizations, but also organizations within Ukraine.
In the attack analyzed by Arctic Wolf, a fake update payload allows an attacker to execute commands on a compromised machine using a reverse shell established against a command and control (C2) server. This includes conducting reconnaissance and dropping a custom Python backdoor codenamed VIPERTUNNEL.

It also provides a DLL loader for RomCom links that launches the Mythic Agent. The Mythic Agent is a key component of the cross-platform post-exploitation red teaming framework that communicates with corresponding servers to support command execution, file manipulation, and more.
Although the attack was ultimately unsuccessful and blocked before it could proceed any further, this development demonstrates RomCom threat actors’ continued interest in targeting Ukraine or organizations providing support to that country, no matter how tenuous the relationship.
“Timeline from infection” [the fake update] “Delivery time for the RomCom loader was less than 30 minutes,” said Jacob Faires. “Delivery will not occur until the target Active Directory domain is verified to match known values provided by the threat actor.”
“The widespread nature of SocGholish attacks and the relative speed with which they progress from initial access to infection make them a powerful threat to organizations around the world.”
Source link