The threat actor known as Bloody Wolf is believed to be involved in a cyber attack campaign targeting Kyrgyzstan with the purpose of delivering the NetSupport RAT since at least June 2025.
As of October 2025, the operation has expanded to include Uzbekistan, Group IB researchers Amirbek Kurbanov and Volen Kayo said in a joint report with Ukuk, a state-owned company affiliated with the Kyrgyz Republic Prosecutor General’s Office. The attacks targeted the financial, government, and information technology (IT) sectors.
“Those threat actors are [Kyrgyzstan’s] “The Ministry of Justice hosted malicious Java Archive (JAR) files designed to deploy the NetSupport RAT through official-looking PDF documents and domain names,” the Singapore-based company said.
“A combination of social engineering and easily accessible tools will allow Bloody Wolf to remain effective while keeping its operational profile low.”

Bloody Wolf is the name assigned to a group of hackers of unknown origin that conducted spear-phishing attacks targeting organizations in Kazakhstan and Russia using tools such as STRRAT and NetSupport. This group is estimated to have been active since at least late 2023.
Targeting Kyrgyzstan and Uzbekistan using similar early access techniques indicates the threat actor’s growing activity in Central Asia, primarily crafting phishing emails impersonating trusted government ministries and distributing weaponized links and attachments.
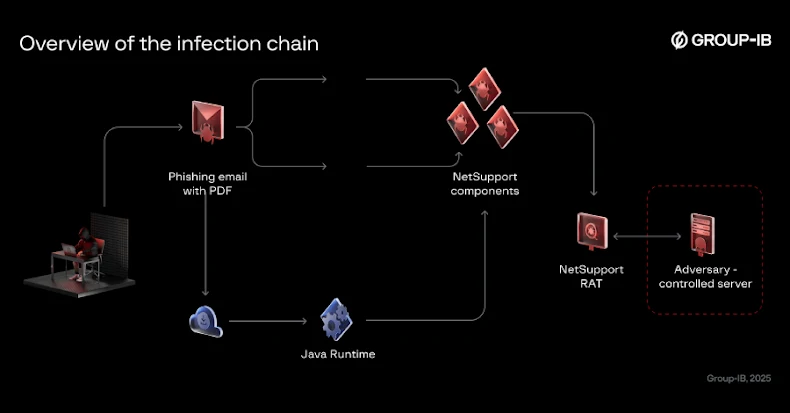
This attack chain follows more or less the same approach in that it tricks the message recipient into clicking a link that downloads a malicious Java Archive (JAR) loader file along with Java runtime installation instructions.
Although the email claims that installation is required to view the documentation, it is actually used to run the loader. Once launched, the loader retrieves the next stage payload (i.e. the NetSupport RAT) from infrastructure under the attacker’s control and sets persistence in three ways:
Create a scheduled task Add a Windows registry value Drop a batch script into the folder “%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup”

The Uzbekistan phase of the campaign is notable for incorporating geofencing restrictions. This redirects international requests to the legitimate data.egov.[.]Uzu’s website. Requests from within Uzbekistan were found to trigger downloads of JAR files from embedded links within PDF attachments.
According to Group-IB, the JAR loader observed in the campaign is built on Java 8, which was released in March 2014. The attackers are believed to be using custom JAR generators or templates to generate these artifacts. The NetSupport RAT payload is an older version of NetSupport Manager from October 2013.
“Bloody Wolf has demonstrated that low-cost, commercially available tools can be armed with sophisticated, regionally targeted cyber operations.” “By leveraging trust in government agencies and leveraging simple JAR-based loaders, the group continues to maintain a strong foothold across Central Asian threats.”
Source link