The threat actor known as Jewelbug has increasingly focused on government targets in Europe since July 2025, even as it continues to attack organizations located in Southeast Asia and South America.
Check Point Research is tracking this cluster under the name Ink Dragon. It is also referred to by the names CL-STA-0049, Earth Alux, and REF7707 in the broader cybersecurity community. The Chinese-aligned hacker group is estimated to have been active since at least March 2023.
“The attacker’s campaign is an aggressive combination of solid software engineering, disciplined operational strategy, and reuse of platform-native tools that blend into regular enterprise telemetry,” the cybersecurity firm said in a technical breakdown published Tuesday. “This combination makes their infiltration both effective and stealthy.”
Eli Smadja, group manager of product research and development at Check Point Software, told Hacker News that the campaign is ongoing and has “impacted dozens of victims, including government agencies and telecommunications organizations across Europe, Asia, and Africa.”
Details about this threat group first emerged in February 2025, when Elastic Security Labs and Palo Alto Networks Unit 42 detailed the use of a backdoor called FINALDRAFT (also known as Squidoor) that can infect both Windows and Linux systems. In recent months, Ink Dragon has also been suspected of a five-month intrusion targeting Russian IT service providers.

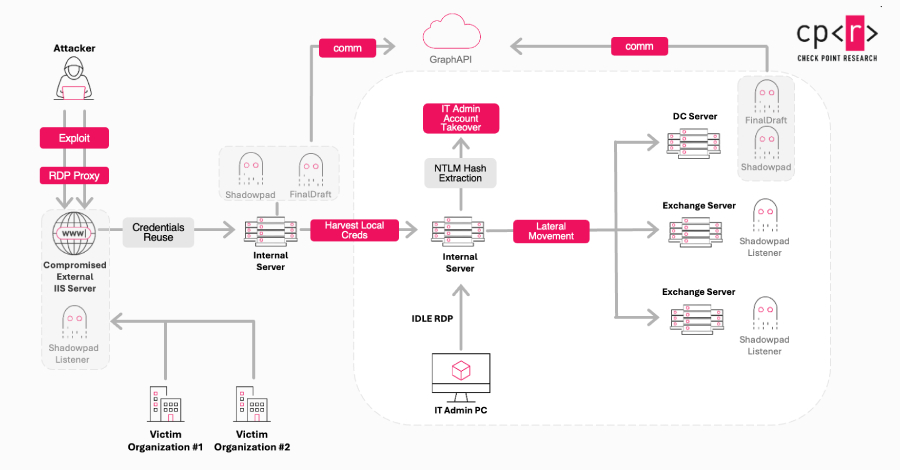
Attack chains launched by adversaries leverage vulnerable services in internet-exposed web applications to drop a web shell, which is then used to deliver additional payloads, such as VARGEIT beacons and Cobalt Strike beacons, to facilitate command and control (C2), discovery, lateral movement, defense evasion, and data leakage.
Another notable backdoor in threat actors’ malware arsenal is NANOREMOTE. It uses the Google Drive API to upload and download files between the C2 server and the compromised endpoint. Check Point said it did not encounter any malware in the intrusions or investigations it observed.
“An attacker may selectively deploy tools from a broader toolkit depending on the victim’s environment, operational needs, and desire to blend into legitimate traffic,” Smadja said.
Ink Dragon also relied on predictable or mismanaged ASP.NET machine key values to perform ViewState deserialization attacks on vulnerable IIS and SharePoint servers and installed a custom ShadowPad IIS listener module to turn these compromised servers into part of the C2 infrastructure, allowing them to proxy commands and traffic to improve process resiliency.
“This design allows attackers to route traffic not only deep inside a single organization’s network, but across different victim networks,” Check Point said. “As a result, one breach can become another hop in a global, multi-layered infrastructure that supports ongoing campaigns elsewhere, merging operational management and strategic reuse of previously compromised assets.”
The listener module also has the ability to execute various commands on the IIS machine, giving an attacker more control over the system for reconnaissance and staging payloads.
In addition to exploiting exposed machine keys to achieve ASP.NET ViewState deserialization, the attacker was found to be armed with a ToolShell SharePoint flaw to drop a web shell onto a compromised server. Other steps performed by Ink Dragon are:
Use the IIS machine key to obtain local administrative credentials and leverage them for lateral movement through the RDP tunnel Create a scheduled task to install the service and establish persistence Dump an LSASS dump and extract the registry hive to achieve privilege escalation Modify host firewall rules to allow outbound traffic and convert infected hosts to a ShadowPad relay network
“In at least one instance, the attacker identified an idle RDP session belonging to a domain administrator who was authenticated via Network Level Authentication (CredSSP) with NTLMv2 fallback. The session remained disconnected but was not logged off, making it very likely that LSASS was holding the associated logon token and NTLM validator in memory,” Check Point said.
“Ink Dragon gained SYSTEM-level access to the host, extracted tokens (and possibly NTLM key material), and reused them to perform authenticated SMB operations. Through these actions, Ink Dragon was able to write to administrative shares and extract NTDS.dit and registry hives, demonstrating that it achieved domain-wide privilege escalation and control.”
Intrusions have been found to rely on numerous components rather than a single backdoor or monolithic framework to establish long-term persistence. These include –
ShadowPad Loader: Used to decrypt and execute the ShadowPad core module in memory CDBLoader: Use the Microsoft Console Debugger (‘cdb.exe’) to execute shellcode and load the encrypted payload LalsDumper: Extract the LSASS dump 032Loader: Used to decrypt and execute the payload FINALDRAFT: Outlook and Microsoft Graph API Updated version C2 of a known remote administration tool that exploits

“This cluster introduced a new variant of the FINALDRAFT malware with enhanced stealth and higher extraction throughput, as well as advanced evasion techniques that enable stealthy lateral movement and multi-stage malware deployment across compromised networks,” Check Point said.
“FINALDRAFT implements a modular command framework where an operator pushes encoded command documents to a victim’s mailbox, and the implant pulls, decrypts, and executes them.”
The cybersecurity firm also noted that it detected evidence of a second threat actor known as REF3927 (also known as RudePanda) in “some” of the same victim environments compromised by Ink Dragon. However, there is no indication that the two clusters are operationally linked. Both intrusion sets are believed to have gained a foothold by exploiting the same initial access method.
“Ink Dragon presents a threat model where the line between ‘compromised host’ and ‘command infrastructure’ no longer exists,” Check Point concluded. “Each scaffold becomes a node in a larger network controlled by the operator; a living mesh that strengthens with each additional casualty.”
“Thus, defenders must view intrusions not just as local compromises, but as potential links in an external ecosystem controlled by attackers. Shutting down a single node is insufficient unless the entire relay chain is identified and dismantled. Ink Dragon’s relay-centric architecture is one of the more mature uses of ShadowPad we’ve observed to date. The blueprint for long-term, multi-organizational access is built on the victims themselves.”
Source link