Cybersecurity researchers have revealed details of an ongoing campaign called KongTuke that uses a malicious Google Chrome extension masquerading as an ad blocker to intentionally crash web browsers, uses ClickFix-like lures to trick victims into executing arbitrary commands, and delivers a previously undocumented remote access Trojan (RAT) called ModeloRAT.
This new escalation of ClickFix is codenamed CrashFix by Huntress.
KongTuke, also tracked as 404 TDS, Chaya_002, LandUpdate808, and TAG-124, is the name given to a traffic distribution system (TDS) known for profiling victim hosts before redirecting them to a payload delivery site that infects the system. Access to these compromised hosts is then passed to other threat actors, including ransomware groups, for subsequent malware distribution.
According to the April 2025 Recorded Future report, cybercrime groups that exploited TAG-124 infrastructure include Rhysida ransomware, Interlock ransomware, and TA866 (also known as Asylum Ambuscade), and this threat actor is also associated with SocGholish and D3F@ck Loader.
In the attack chain documented by the cybersecurity firm, victims allegedly searched for ad blockers when they were served a malicious ad that redirected them to an extension hosted on the official Chrome Web Store.
The browser extension in question, NexShield – Advanced Web Guardian (ID: cpcdkmjddociqdkbbeiaafnpdbdafmi), masquerades as the “ultimate privacy shield” and claims to protect users from ads, trackers, malware, and intrusive content on web pages. It has been downloaded at least 5,000 times. It is no longer available for download.

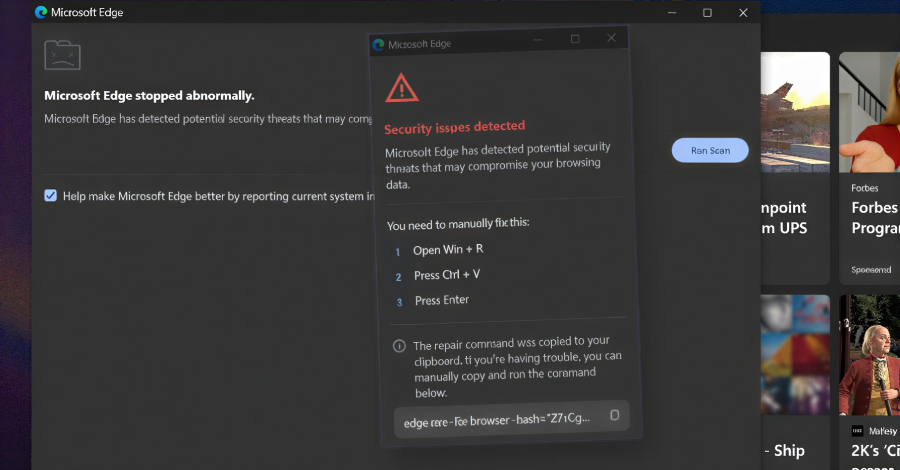
According to Huntress, the extension is a near-identical clone of uBlock Origin Lite version 2025.1116.1841, a legitimate ad blocker add-on available for all major web browsers. It is designed to display a fake security alert that claims the browser has “hanged” and prompts users to run a “scan” to remediate potential security threats detected by Microsoft Edge.
If the user chooses to run the scan, the victim will be given the[ファイル名を指定して実行]A fake security warning opens a dialog instructing you to paste the displayed command that you have already copied to your clipboard and run it. This completely freezes the browser and launches a denial of service (DoS) attack that creates a new runtime port connection through an infinite loop that repeatedly triggers 1 billion iterations of the same step, causing the browser to crash.
This resource exhaustion technique causes excessive memory consumption, causing the web browser to become slow, unresponsive, and eventually crash.
Once installed, this extension is designed to send a unique ID to an attacker-controlled server (‘nexsnield’).[.]com”) to enable operators to track victims. Additionally, it employs a delayed execution mechanism, ensuring that the malicious behavior is only triggered within 60 minutes of being installed. Thereafter, the payload is executed every 10 minutes.
Researchers Anna Pham, Tanner Phillip, and Dani Lopez said, “Popups only appear when you start the browser after the browser has become unresponsive.” “Before performing a DoS, a timestamp is stored in local storage. When the user kills and restarts the browser, the startup handler checks this timestamp and, if present, displays a CrashFix popup and removes the timestamp.”
“DoS is executed only if the UUID is present (implying that the user is being tracked), the C2 server successfully responds to the fetch request, and the pop-up window is opened at least once and then closed. This last condition may be intentional to allow the user to interact with the extension before triggering the payload.”
Ultimately, each time the victim kills and restarts the browser after it becomes unresponsive due to a DoS attack, it creates its own loop and activates the false alert. If the extension is not removed, the attack will be triggered again after 10 minutes.
This popup also incorporates various anti-analysis techniques that disable right-click context menus and prevent attempts to launch developer tools using keyboard shortcuts. The CrashFix command uses a legitimate Windows utility, Finger.exe, to retrieve and execute the next stage payload from the attacker’s server (‘199.217.98’).[.]KongTuke’s use of the Finger command was documented by security researcher Brad Duncan in December 2025.
The payload received from the server is a PowerShell command configured to retrieve a secondary PowerShell script. This uses multiple layers of Base64 encoding and XOR operations to take pages from SocGholish’s playbook and hide the next stage of the malware.
Decrypted Blob scans running processes for over 50 analysis tools and virtual machine indicators and immediately stops execution if found. It also checks whether the machine is domain-joined or standalone and sends an HTTP POST request containing the two pieces of information to the same server.
List of installed antivirus products Flag with value “ABCD111” for standalone “WORKGROUP” machines and “BCDA222” for domain-joined hosts

In this case, the compromised system is marked as domain-joined and KongTuke’s attack chain culminates in the deployment of ModeloRAT, a full-featured Python-based Windows RAT that uses RC4 encryption for command and control (C2) communications (‘170.168.103’)[.]208” or “158.247.252”[.]178″) uses the registry to set persistence and facilitate the execution of binaries, DLLs, Python scripts, and PowerShell commands.
ModeloRAT has the ability to update or terminate itself upon receiving a self-update (“VERSION_UPDATE”) or termination (“TERMINATION_SIGNAL”) command. It also implements various beacon logic to fly under the radar.
“For normal operations, a standard interval of 300 seconds (5 minutes) is used,” Huntress said. “When the server sends the activation configuration command, the implant enters active mode and performs fast polling at configurable intervals (default 150 ms).”
“After six or more consecutive communication failures, the RAT backs off to an extended interval of 900 seconds (15 minutes) to avoid detection. When recovering from a single communication failure, a 150 second reconnection interval is used before resuming normal operation.”
Targeting domain-joined machines with ModeloRAT suggests that KongTuke is targeting corporate environments to facilitate deeper access, but users on standalone workstations are exposed to another multi-stage infection sequence that ends with the C2 server responding with a “TEST PAYLOAD!!!!” message, indicating that it may still be in the testing phase.
“KongTuke’s CrashFix campaign demonstrates how threat actors continue to evolve their social engineering tactics,” the cybersecurity firm concludes. “By impersonating a trusted open source project (uBlock Origin Lite), they constructed a self-sustaining infection loop that preyed on user dissatisfaction by intentionally crashing users’ browsers and offering fake fixes.”
Source link