The Middle East and North Africa have been targeting new campaigns since September 2024 that will provide a fixed version of known malware called Asyncrat.
“The campaign to distribute malware using social media is related to the current geopolitical climate of the region,” Klimentiy Galkin and Stanislav Pyzhov said in an analysis released last week. “Attackers will host malware on legitimate online file sharing accounts or telegram channels specially configured for this purpose.”
The campaign is estimated to have charged around 900 casualties since fall 2024, the Russian cybersecurity company adds, demonstrating its widespread nature. The majority of the victims are in Libya, Saudi Arabia, Egypt, Turkey, the United Arab Emirates, Qatar and Tunisia.
Activities caused by a threat actor called Desert Dexter were discovered in February 2025. This involves creating temporary accounts and news channels mainly on Facebook. These accounts are used to publish advertisements that contain links to file sharing services or Telegram channels.

The link redirects users to a version of Asyncrat malware that has been modified to include offline keyloggers. Search for 16 different cryptocurrency wallet extensions and applications. Communicate with the telegram bot.
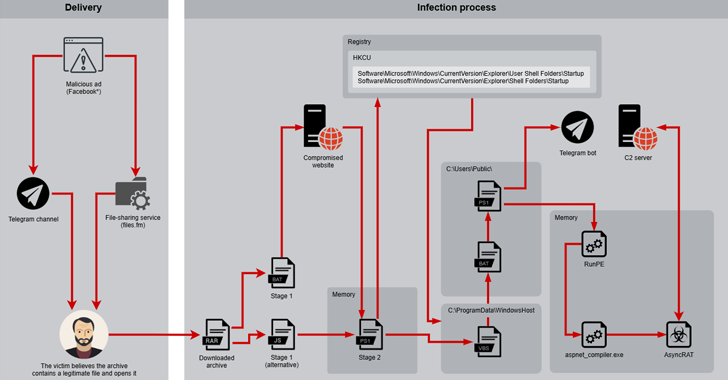
A kill chain starts with a RAR archive containing batch scripts or JavaScript files. It is programmed to run a PowerShell script that is responsible for triggering the second stage of the attack.
Specifically, you will exit the processes associated with various .NET services that may prevent malware from starting, remove the extensions BAT, PS1, and VBS from the “C:\ProgramData\Windowshost” and “C:\Users\public” folders, and create a new VBS file with C:\WindowsData\Users\bat and PS1 files.
The script then launches the Asyncrat payload by establishing system persistence, collecting and removing system information into a telegram bot, taking a screenshot, and finally injecting it into the “ASPNET_COMPILER.EXE” executable.

While the Arabic comments in JavaScript files suggest their potential, it is currently unknown who is behind the campaign.
Further analysis of the messages sent to the telegram bot revealed a screenshot named “Dextermsi” of the attacker’s own desktop. It features a PowerShell script and a tool named Luminosity Link Rat. Also present in the Telegram Bot is a link to a telegram channel named “Dexterlyly,” suggesting that the threatening actor may be from Libya. The channel was created on October 5th, 2024.
“The majority of victims are ordinary users, including employees in the following sectors: oil production, construction, information technology; [and] Agriculture,” the researcher said.

“The tools Desert Dexter uses aren’t particularly sophisticated. However, the combination of Facebook ads and legal services and references to geopolitical circumstances has caused many devices to be infected.”
This development comes as Qianxin revealed details of a spear fishing campaign called the Sea Sightseeing Operation. It has been found to target Chinese scientific research institutions with the aim of providing a backdoor that can harvest sensitive information related to marine science and technology.
This activity is attributed to a cluster named UTG-Q-011, a subset within another hostile group called CNC groups that share tactical overlap with patchwork, a threat actor from India.
Source link