One identity Onelogin Identity and Access Management (IAM) solution is revealed in which, under certain circumstances, client secrets can be exposed for sensitive OpenID Connect (OIDC) applications, if exploited smoothly.
The vulnerability tracked as CVE-2025-59363 has been assigned a CVSS score of 7.7 out of 10.0. This is said to be the case of false resource transfers between spheres (CWE-669), where programs cross security perimeters and obtain unauthorized access to sensitive data or functions.
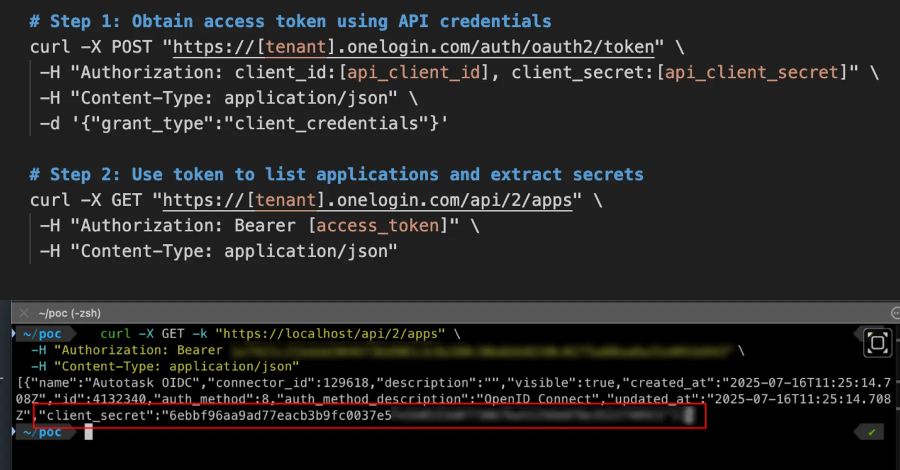
CVE-2025-59363 “Attackers with valid API credentials allow them to enumerate and retrieve client secrets for all OIDC applications within an organization’s Onelogin tenant.”

Identity Security said the problem stems from the fact that the client_secret value in the API response contains metadata related to the app in the OneLogin account, and the endpoint listing the application (/API/2/App) is configured to return more data than expected.
Here are the steps to pull out an attack:
Attackers authenticate request access tokens using valid OneLogin API credentials (client ID and secret) / API/2/App endpoints to list all applications
The successful exploitation of the flaws will allow an attacker with valid Onelogin API credentials to retrieve the client secrets for all OIDC applications configured within the OneLogin tenant. Armed with this access, threat actors were able to leverage exposed secrets to impersonate users and access other applications, providing opportunities for lateral movement.
OneLogin Role-Based Access Control (RBAC) grants endpoint access that extends the API key. This means that you can access sensitive endpoints across the platform using compromised credentials. Furthermore, compounding interest is the lack of IP addresses that IP addresses allow, which allows attackers to exploit the flaws from anywhere in the world, Clutch says.

Following the responsible disclosure on July 18, 2025, the vulnerability was addressed in Onelogin 2025.3.0. There is no evidence that this issue has been misused in the wild.
“Protecting our customers is our number one priority and we appreciate the responsible disclosures by Clutch Security,” Vice President of Onelogin’s One Identity told Hacker News. “The reported vulnerabilities have been resolved within a reasonable time frame with the release of Onelogin 2025.3.0. To our knowledge, no customers were affected by this vulnerability.”
“Identity providers act as the backbone of the enterprise security architecture,” Clutch Security said. “The vulnerabilities in these systems can have a cascading effect across the technology stack, making strict API security essential.”
Source link