Cybersecurity researchers have detailed a new dual-vector campaign that leverages stolen credentials to deploy legitimate remote monitoring and management (RMM) software to gain persistent remote access to compromised hosts.
“Instead of deploying custom viruses, attackers are circumventing security boundaries by weaponizing necessary IT tools that administrators trust,” said Jeewan Singh Jalal, Prabhakaran Ravichandhiran, and Anand Bodke, researchers at KnowBe4 Threat Labs. “It turns legitimate remote monitoring and management (RMM) software into a persistent backdoor by stealing the system’s ‘skeleton key’.”
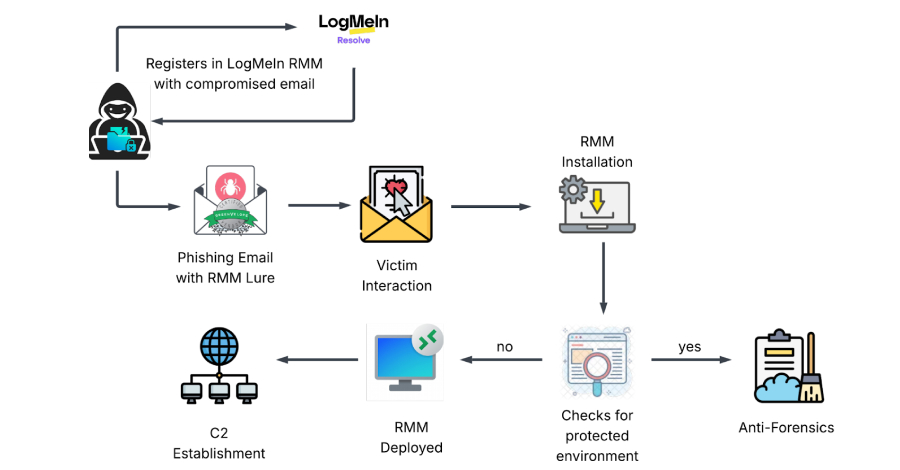
This attack unfolds in two different waves. Attackers use fake invitation notifications to steal victims’ credentials, which they then use to deploy RMM tools to establish permanent access.

The fake email appears to be an invitation from a legitimate platform called Greenvelope, and is designed to trick recipients into clicking a phishing URL designed to collect login information for Microsoft Outlook, Yahoo!, and AOL.com. Once this information is obtained, the attack proceeds to the next phase.
Specifically, the attacker uses a compromised email to register with LogMeIn and generate an RMM access token. This token is deployed in subsequent attacks via an executable named ‘GreenVelopeCard.exe’ to establish persistent remote access to the victim system.
The binary, signed with a valid certificate, contains JSON configuration that silently installs LogMeIn Resolve (formerly known as GoTo Resolve) and serves as a conduit to connect to an attacker-controlled URL without the victim’s knowledge.
Once the RMM tool is deployed, attackers can use remote access as a weapon to modify service settings and allow them to run on Windows with unrestricted access. The attack also establishes a hidden scheduled task that automatically launches the RMM program even if the user manually terminates it.
To combat this threat, organizations are encouraged to monitor unauthorized RMM installation and usage patterns.
Source link