Cybersecurity researchers are warning of a new campaign that combines ClickFix lures with fake adult websites to trick users into running malicious commands under the guise of an “important” Windows security update.
“The campaign utilizes fake adult websites (xHamster, a PornHub clone) as a phishing mechanism and is likely distributed via malvertising,” Acronis said in a new report shared with Hacker News. “The adult themes and possible connections to questionable websites increase the psychological pressure on victims to comply with the installation of sudden ‘security updates’.”
ClickFix-style attacks have proliferated over the past year, typically using prompts for technical fixes or completing CAPTCHA validation checks to trick users into running malicious commands on their machines. According to Microsoft data, ClickFix is the most common initial access method, accounting for 47% of attacks.
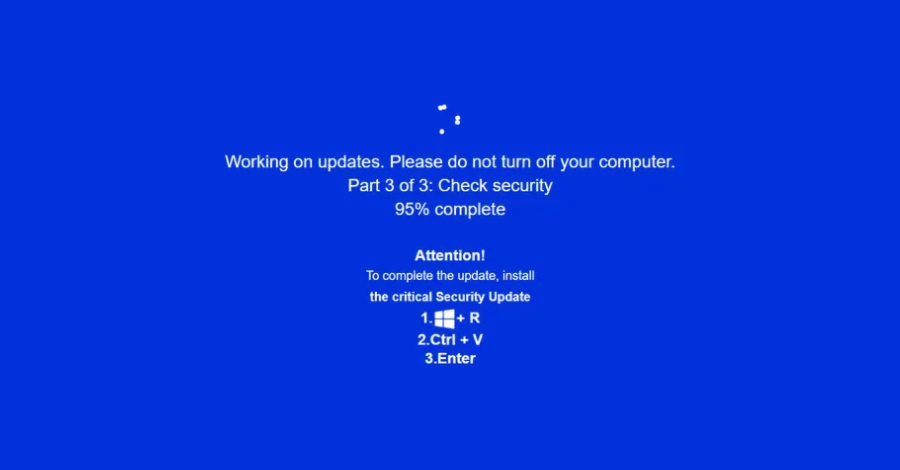
The latest campaign displays a highly convincing fake Windows update screen in an attempt to trick victims into running malicious code, showing that attackers are moving away from the lure of traditional robot checks. The operation is codenamed “JackFix” by a Singapore-based cybersecurity firm.
Perhaps the most concerning aspect of this attack is that the fake Windows update alert hijacks the entire screen, giving the victim access to Windows[ファイル名を指定して実行]What it does is open a dialog that tells you to press Ctrl + V and then press Enter, which triggers the infection sequence.

The starting point of the attack is believed to be fake adult sites that redirect unsuspecting users through malvertising and other social engineering techniques. Then, out of the blue, you get an “emergency security update.” Some versions of these sites were found to contain developer comments in Russian, suggesting the possible presence of Russian-speaking attackers.
“The Windows Update screen is created entirely using HTML and JavaScript code and pops up as soon as the victim interacts with any element on the phishing site,” security researcher Eliad Kimhi said. “This page attempts to go full screen via JavaScript code, while also creating a rather convincing Windows Update window with a blue background and white text, reminiscent of Windows’ infamous blue screen of death.”
What’s notable about this attack is that it relies heavily on obfuscation to hide ClickFix-related code, and blocks users from escaping full-screen alerts by disabling the Escape and F11 buttons in addition to the F5 and F12 keys. However, a logic flaw allows users to press the Escape and F11 buttons to exit full screen.
The first command executed is an MSHTA payload that is launched using the legitimate mshta.exe binary. It contains JavaScript designed to run PowerShell commands and retrieve another PowerShell script from a remote server. These domains are designed so that if you go directly to these addresses, users will be redirected to benign sites such as Google or Steam.
“The site will only respond with the correct code if you access it via the irm or iwr PowerShell commands,” Acronis explained. “This creates an additional layer of obfuscation and anti-analysis.”
 UAC request to grant administrator privileges to attacker
UAC request to grant administrator privileges to attacker
The downloaded PowerShell scripts also incorporate various obfuscation and anti-analysis mechanisms, one of which is the use of garbage code that complicates analysis efforts. It also attempts privilege escalation and creates Microsoft Defender Antivirus exclusions for command and control (C2) addresses and paths where the payload is staged.
To achieve privilege escalation, the malware uses the Start-Process cmdlet in conjunction with the “-Verb RunAs” parameter to launch PowerShell with administrative privileges and continuously prompt for permissions until permission is granted by the victim. If this step is successful, the script is designed to drop an additional payload, such as a simple remote access trojan (RAT) programmed to connect to a C2 server, possibly to drop more malware.
PowerShell scripts have also been observed delivering up to eight different payloads, which Acronis describes as “the most egregious example of spray-and-pray.” These include Rhadamanthys Stealer, Vidar Stealer 2.0, RedLine Stealer, Amadey, and other unspecified loaders and RATs.
“If only one of these payloads is successfully executed, the victim risks losing passwords, cryptocurrency wallets, etc.,” Kimhy said. “In the case of some of these loaders, the attacker may choose to bring other payloads into the attack, and the attack could quickly escalate further.”

The disclosure came as Huntress detailed a multi-step malware execution chain that begins with a ClickFix decoy disguised as a Windows update and then deploys stealer malware like Lumma and Rhadamanthys by hiding the final step within an image, a technique known as steganography.
As with the campaign above, it will be copied to the clipboard and[実行]ClickFix commands pasted into the dialog use mshta.exe to execute a JavaScript payload that can run remotely hosted PowerShell scripts directly in memory.
PowerShell code is used to decrypt and launch the .NET assembly payload. This loader, called Stego Loader, acts as a conduit for executing DonutPak’s shellcode hidden within the embedded and encrypted PNG file. The extracted shellcode is injected into the target process and ultimately deploys Lumma or Rhadamanthys.

Interestingly, we can see that one of the domains listed by Huntress is used to retrieve a PowerShell script (‘securitysettings’).[.]live”) was also flagged by Acronis, suggesting that these two activity clusters may be related.
“Threatening attackers frequently change the URI used to host the initial mshta.exe stage (e.g. /tick.odd, /gpsc.dat, /ercx.dat),” security researchers Ben Folland and Anna Pham said in the report.
“Furthermore, the attacker moved away from the second-tier host in the domain’s security settings.[.]Not live, hosted on xoiiasdpsdoasdpojas[.]com, but both point to the same IP address, 141.98.80.[.]175, was also used for the first stage delivery [i.e., the JavaScript code run by mshta.exe]. ”
ClickFix has been so successful because it relies on a simple and effective method of tricking users into infecting their machines and bypassing security controls. Organizations can train employees to better spot threats and update Windows through registry changes or Group Policy.[ファイル名を指定して実行]You can prevent such attacks by disabling the box.
Source link