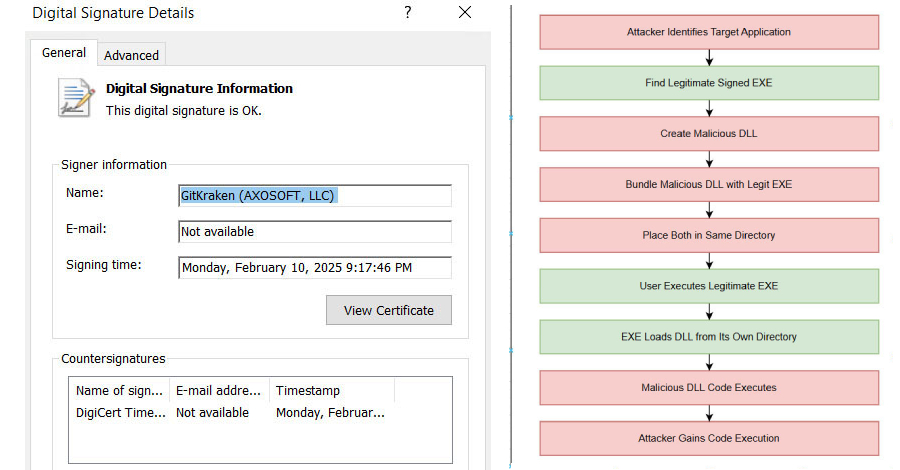
Security experts have detailed an active malware campaign that exploits a DLL sideloading vulnerability in legitimate binaries related to the open source c-ares library to bypass security controls and deliver a wide range of commodity Trojans and stealers.
“The attacker achieves evasion by combining the malicious libcares-2.dll with a signed version of the legitimate ahost.exe (often renamed) to execute code,” Trellix said in a report shared with The Hacker News. “This DLL sideloading technique allows malware to evade traditional signature-based security defenses.”
This campaign has been observed distributing a wide variety of malware, including Agent Tesla, CryptBot, Formbook, Lumma Stealer, Vidar Stealer, Remcos RAT, Quasar RAT, DCRat, and XWorm.
Targets of this malicious activity include employees in management positions in commercial and industrial sectors such as finance, procurement, supply chain, oil and gas, and import/export, with invitations written in Arabic, Spanish, Portuguese, Farsi, and English, suggesting that the attack is localized.

The attack relies on placing a malicious version of the DLL in the same directory as the vulnerable binary, taking advantage of the fact that it is susceptible to search order hijacking to execute the contents of the malicious DLL in place of the legitimate DLL, giving the threat actor the ability to execute code. The “ahost.exe” executable used in the campaign is signed by GitKraken and is typically distributed as part of GitKraken’s desktop application.
Analysis of artifacts in VirusTotal reveals “RFQ_NO_04958_LG2049 pdf.exe”, “PO-069709-MQ02959-Order-S103509.exe”, “23RDJANUARY OVERDUE.INV.PDF.exe”, “Sales Agreement”, and others. po-00423-025_pdf.exe” and “Fatura da DHL.exe” demonstrate the use of invoice and request for quotation (RFQ) themes to trick users into opening.
“This malware attack highlights the growing threat of DLL sideloading attacks that exploit trusted signed utilities like GitKraken’s ahost.exe to bypass security defenses,” Trellix said. “By leveraging legitimate software and exploiting its DLL loading process, attackers can silently deploy powerful malware such as XWorm and DCRat, allowing persistent remote access and data theft.”
The disclosure comes after Trellix reported a spike in Facebook phishing scams that use browser-in-the-browser (BitB) technology to simulate Facebook’s authentication screen and trick unsuspecting users into entering their credentials. It works by creating a fake pop-up inside the victim’s legitimate browser window using an iframe element, making it virtually impossible to distinguish between genuine and fake login pages.
“Attack attacks often begin with a phishing email disguised as a communication from a law firm,” researcher Mark Joseph Marti said. “The emails typically contain a fake legal notice about the infringing video and include a hyperlink that appears to be a Facebook login link.”
As soon as victims click on the shortened URL, they are redirected to a fake Meta CAPTCHA prompt asking them to sign in to their Facebook account. This triggers a pop-up window that uses the BitB method to display a fake login screen designed to collect credentials.
Other variants of social engineering campaigns utilize phishing emails that claim copyright violations, unusual login warnings, imminent account shutdown due to suspicious activity, or potential security vulnerabilities. These messages are designed to create a false sense of urgency and lure victims to a page hosted on Netlify or Vercel to obtain their credentials. There is evidence to suggest that the phishing attack may have been ongoing since July 2025.
“This method takes advantage of users’ familiarity with authentication flows by creating a custom-built fake login pop-up window within the victim’s browser, making credential theft nearly impossible to detect visually,” Trellix said. “The key change lies in the exploitation of trusted infrastructure, leveraging legitimate cloud hosting services and URL shortening tools such as Netlify and Vercel to bypass traditional security filters and give phishing pages a false sense of security.”
This discovery coincides with the discovery of a multi-stage phishing campaign that leverages Python payloads and TryCloudflare tunnels to distribute AsyncRAT via Dropbox links pointing to ZIP archives containing Internet shortcut (URL) files. Campaign details were first documented by Forcepoint X-Labs in February 2025.

“The initial payload, a Windows Script Host (WSH) file, was designed to download and execute additional malicious scripts hosted on WebDAV servers,” Trend Micro said. “These scripts facilitated the download of batch files and further payloads, ensuring a seamless and persistent infection routine.”
Notable aspects of this attack are the exploitation of Living-off-the-land (LotL) techniques using Windows Script Host, PowerShell, native utilities, and the exploitation of Cloudflare’s free tier infrastructure to host WebDAV servers and evade detection.

The script staged in the TryCloudflare domain is designed to install a Python environment, establish persistence via a Windows startup folder script, and inject AsyncRAT shellcode into the “explorer.exe” process. In parallel, a decoy PDF is displayed to the victim, fooling them into thinking that a legitimate document has been accessed.
“The AsyncRAT campaigns analyzed in this report demonstrate the growing sophistication of attackers who exploit legitimate services and open-source tools to evade detection and establish persistent remote access,” Trend Micro said. “By leveraging Python-based scripts and exploiting Cloudflare’s free tier infrastructure to host malicious payloads, the attackers were able to bypass traditional security controls and hide their activity on trusted domains.”
Source link